Working for a secure Swiss Internet
Thousands of people in Switzerland fall victim to cyberattacks every year. Last year alone, Â̲èÖ±²¥ handled 2,500 cases of abuse. More worrying than the number of attacks is the increasing technical sophistication. A glimpse behind the scenes shows how Â̲èÖ±²¥ unmasks ever more perfidious cyberthreats every day.

I’ve been working at the Â̲èÖ±²¥ registry for six years as a specialist in combating the abuse of .ch and .li domain names. I have witnessed first-hand how cybercriminals are developing ever more perfidious tactics to line their pockets from their victims.
Malware and phishing are becoming increasingly sophisticated
When I joined Â̲èÖ±²¥ in 2019, the cases of abuse were comparatively simple. We detected phishing simply by surfing a website in a secure environment. We detected malware directly in the website’s source code using known patterns. Complicated cases were the exception.
However, the complexity of abuse cases has increased significantly in recent years. The criminals have become more cunning. Today, they specifically block IP addresses of security professionals, they use software to detect analysis systems, and they hide their malware behind legitimate services, as we will see in an example later.
When branded shoes become a trap
My day as a Domain Abuse Handler starts with checking the abuse reports I received. One message immediately catches my eye: Blocking request pursuant to (Swiss Ordinance on Internet Domains). It’s about a fake shop selling cheap branded trainers. But if you order a pair of your dream trainers for a fifth of the original price, you can be sure you’ll never receive a parcel. An by the Federal Office of Communications (OFCOM) is asking us to block this Swiss domain name. I comply with this, and the fake shop is no longer accessible on the Internet.
When it comes to fraud, we as a registry have no authority of our own. Only a recognised authority, usually a police force, is authorised to issue an injunction and demand the blocking of a domain name. Our areas of expertise are strictly regulated in the VID. It contains, so to speak, our Ten Commandments – even if it contains more than ten paragraphs.
The phishing classics
The next case is a reported phishing website. The criminals imitate well-known brands or organisations in order to gain access to their victims’ personal or credit card details. According to the report, this time it was a phishing case against Swiss Post. Since almost everyone in Switzerland comes into contact with Swiss Post and regularly receives parcels, this scam works particularly well.
So, I’m dealing with a classic, and yet I stut. Amongst other top-level domains such as .com or .top, we come across dozens of such phishing websites every day. Under .ch, they are comparatively rare.
The problem with analysis systems
Our custom analysis system has already analysed the website. I take a look at the results: 404 – The website cannot be found. This is a common pattern when criminals block our publicly known IP addresses. They try to prevent Â̲èÖ±²¥ from detecting their malware. I therefore use our VPN gateways to resolve the domain from other IP addresses. No luck. Again, just 404s.
My next tactic is to use a secure browser environment to hide our analytics system and conceal my origin by accessing the website via the Tor network. Bingo! A copy of the official Swiss Post website is displayed with a request to pay CHF 3.28 in customs fees. Upon clicking on ‘Pay now’, input fields for credit card details appear.
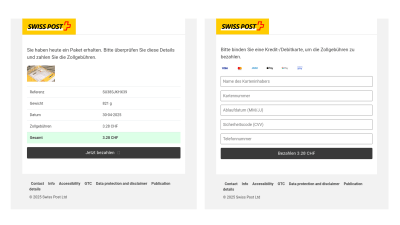
As no valid address and telephone number were provided when the domain name was registered, I suspect that the criminals themselves have registered the domain name: a so-called abusive registration. I block the domain name immediately. As a result, the website is no longer accessible on the Internet, and it can no longer cause any damage. At the same time, I ask the domain name holder to disclose his identity. After the deadline has passed and the identity request has not been answered, we will revoke the registration of the domain name.
Malware remains the biggest challenge
I move on to the malware cases where criminals spread malware via mostly compromised websites. This is where my work really begins. In Switzerland, there are four cases of malware for every phishing case. These are also much more complex. Like the case I am dealing with today, which was reported by one of our many threat intelligence partners.
Our analysis system doesn’t detect the malware. Even when I look at the code more closely, I can’t detect any malware. So, I call my colleague Robin for help. He is an experienced malware expert and knows the current threat situation like a tailor knows his sewing box.
Robin explains to me: ‘This is a new attack tactic used by ClearFake. They access the financial blockchain ‘Binance’ and download obfuscated code from it. This is executed in the browser and downloads the ClearFake browser infection, which in turn infects the victim’s computer with malware. I’m working on automating the detection of this pattern.’

The stored data of the domain name holder looks legitimate in this case. So my suspicion is that criminals have compromised his web server and taken control of the website. I am going to notify the holder and allow 24 hours to remove the malware. If he does not comply with our request within this period, I have to temporarily block the website in accordance with the rules set out in the VID to prevent website visitors from becoming infected with the malware.
After two hours, the holder removed the compromise. That was quick. But a lingering aftertaste remains, and I wonder:
- Is all the malware removed?
- Did the holder miss a backdoor?
- Has the holder changed all the system passwords?
- Are all components up to date now?
- Are there no insecure plugins from third-party providers in use?
I know it is the website operator’s responsibility to clarify this. Â̲èÖ±²¥ has no access to their systems and cannot perform these checks. However, we are happy to provide website operators with important security information at .
Working together for a secure Swiss Internet
The cybercriminals are clever, and so are we. However, we rely on everyone to report suspicious websites to the National Cyber Security Centre’s (NCSC) reporting office at . Only by working together can we successfully combat the threats to the Swiss Internet.